Use Case II
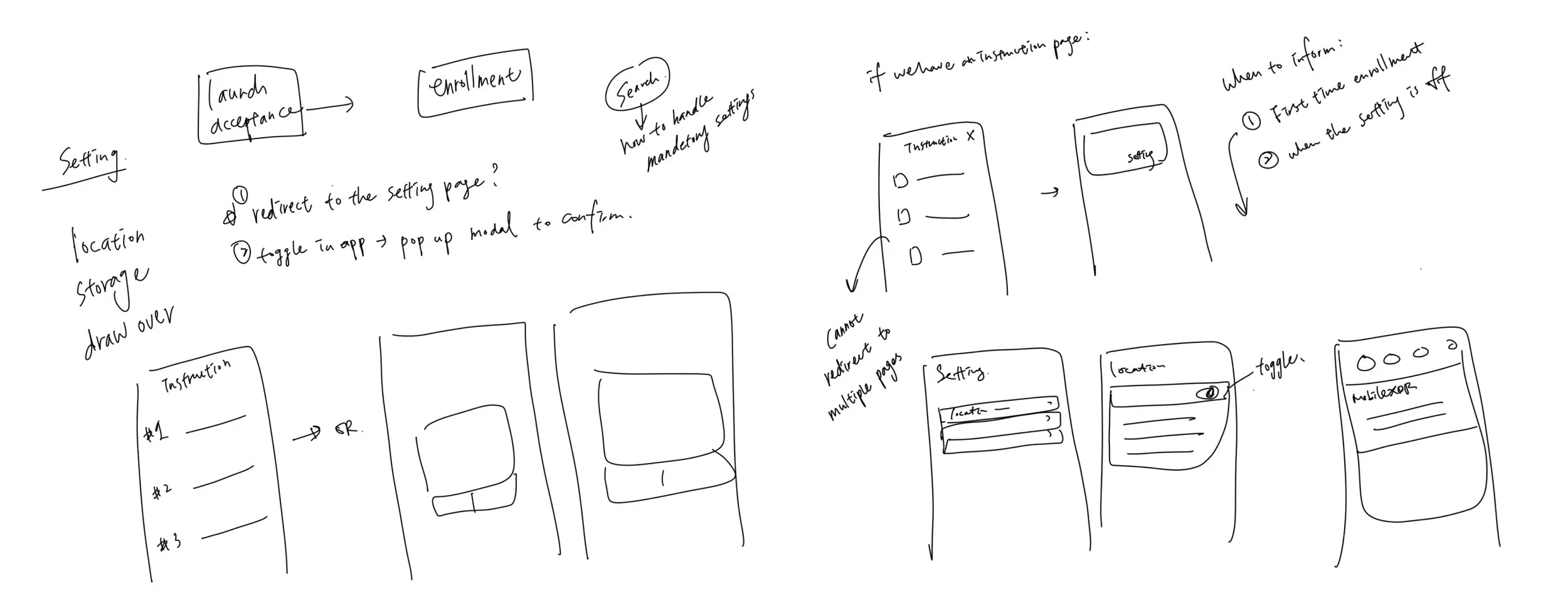
As a mobile security admin, I need the end user to complete a few settings in the device to enable the agent detection capability.
How might we remind the end user to complete the mobile settings, so that the security features can work as how it is set by the mobile security admin?
The required settings of the app may be on and off over time based on the user’s usage. For instance, a VPN needs to be enabled so that the security modal can collect data via the pathway but it may be disabled by the end user. However, a user is only expected to open the app under three circumstances:
When the end user first enrol the device to the solution
When the end user sees the notification when the app detects suspicious activity and has required action to take
When requested by the security admin to copy the error code for troubleshooting
I proposed a few user flows guiding the user to finish the pre-settings, such as showing a pop-up notification when opening the app or having a page with the set-up guidance. After an internal validation, we agreed that adding a new navigation tab in the app may be easily overlooked. Besides, in most cases, the app page may become futile when the user has all set up.